This article was peer reviewed by Adrian Sandu. Thanks to all of SitePoint’s peer reviewers for making SitePoint content the best it can be!
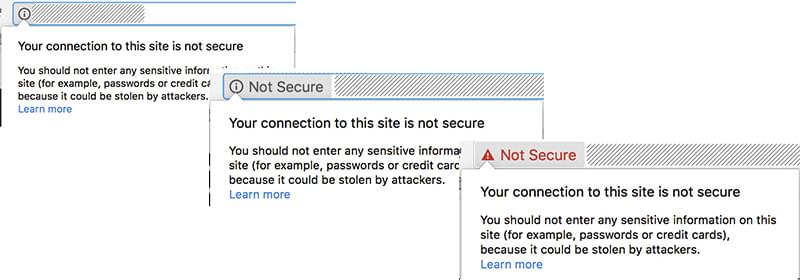
Ever since Google started taking HTTPS into consideration as a ranking factor in 2014, people have slowly been switching their sites over to use encrypted connections. This can be one reason to set up SSL to secure WordPress – SEO. However, as of January 2017, Google made things a bit more serious by having Chrome indicate that sites which still use HTTP are insecure. When a site uses a form that gathers potentially private user data, such as login credentials, there’s an even more stringent notification showing that the site is not secure.
These notifications are still in a gray color, but it probably won’t take long before we start seeing the red notification messages for all of these situations. These red messages are already visible when there is, in fact, an SSL certificate in place, but it can’t be verified. And it isn’t just Chrome — browsers like Safari, Internet Explorer and Firefox all have similar ways of showing the security, or the lack of security, on a site.
An added benefit is having your site served over HTTPS is that you can make use of HTTP/2, for which SSL is a requirement.
So there’s no better time than now to make the switch. In this article I will show you three ways to get the green padlock:
- Using CloudFlare to secure your site with a generic SSL certificate the easy way.
- Using Let’s Encrypt to get domain level encryption.
- Getting an Extended Validation SSL to achieve the highest level of certificate, wíth your business name shown instead of just the “Secure” notice.
Securing WordPress the Easy Way: CloudFlare SSL
Using CloudFlare to secure your site is the easiest way to do it, but it does have some caveats. Kray Mitchell did a great tutorial on how to install CloudFlare, along with its Universal SSL feature.
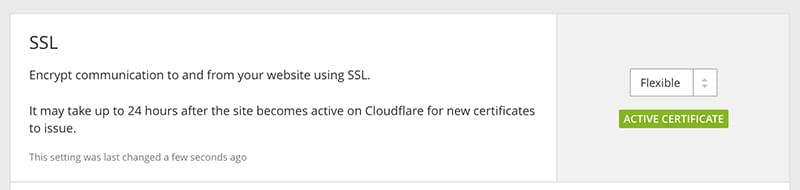
The process is very simple: Sign up for CloudFlare, change the DNS of your site to activate CloudFlare, and turn on “Flexible SSL” in the “Crypto” section.
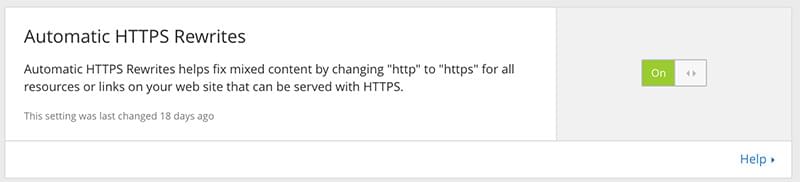
To make it even easier, you can have CloudFlare overwrite links to non-secure URLs with the HTTPS version to prevent mixed content warnings. You do this by turning on “Automatic HTTPS Rewrites,” at the bottom of the “Crypto” section.
If you install the CloudFlare WordPress plugin you can specify some of the required settings from within the WP admin. Additionally it helps to overcome an infinite loop that’s triggered sometimes when changing the URL structure to HTTPS, by modifying the header. The plugin is also the easiest way to setup Server Push, which is one of the main benefits of HTTP/2.
It is really that simple! But there are two important points to acknowledge:
- Flexible SSL only encrypts traffic between the browser and CloudFlare. This means the traffic between CloudFlare and your site (on the origin server) is unencrypted, which still leaves room for a “Man-in-the-Middle” attack. This method also isn’t allowed when you’re using forms to sensitive information like credit card data or passwords. To be clear: You can’t use this method for e-commerce sites.
- CloudFlare is using a shared SSL certificate, which means that your visitors won’t be able to verify it’s really you behind the scenes. Even though most visitors won’t go through the effort of checking a certificate, it’s still something to keep in mind. Again, when it comes to becoming PCI compliant for e-commerce (maintaining an SSL certificate is one of the steps), this isn’t allowed.
CloudFlare also offers “Full” and “Full (Strict)” SSL protection. The latter also validates the certificate on the origin server, which at least mitigates the first point above. However, it is still a shared certificate. For $5 per month, you can order a dedicated certificate, but there are cheaper ways to do this; for example, using Let’s Encrypt, which is covered later in this post.
CloudFlare Flexible SSL is a simple way to get your site secure, but, as you’ve seen here, it gives a bit of a false sense of security. While this will prevent any punishment Google can come up with, it won’t always be the best way to actually secure your site and its visitors. But, for a basic informational site, this will do the trick.
Domain Validation for Free: Let’s Encrypt
Let’s Encrypt is a non-profit certificate authority where you can get a free Domain Validation SSL certificate. This means you will be issued a certificate for your own domain name, instead of a shared SSL. And because of the growing support of many large and medium sized hosting providers, the steps to implement it and create a more secure WordPress site are growing less difficult.
On a mission to make the web more secure, Let’s Encrypt has automated the process of issuing certificates at the domain level, which is the lowest level of protection. There’s a manual route to get the certificate yourself. Or you could ask your host to assist you. Most hosting providers are willing to provide an SSL certificate installation for free, or for just a nominal fee. The easiest way is to find a host which offers Let’s Encrypt support.
With Let’s Encrypt certificates, you have to keep in mind that they expire every 90 days. In their Why 90 Days post, the organization explains that the main reason they do this is because it limits damage from key compromise, and mis-issuance. They also think it encourages automation, which many supported providers have in place.
While their reasons are valid, it requires you to either ensure your certificate is automatically renewed, whether by your hosting provider or by a process that you have set up, or to do this manually yourself every 90 days. If not, you’ll still end up with the dreaded “insecure” message.
WordPress hosts like WPEngine, Dreamhost, and SiteGround either have this automation already in place, or instructions on to have their support handle it for you. Most decent hosts shouldn’t charge you for the Let’s Encrypt certificate or the installation.
Dealing with Mixed Content
There’s one caveat, though, which you will also experience with the EV certificates covered later in this post. Unlike with CloudFlare, you have to make sure yourself that all resources are loaded over HTTPS. If not, you will see the dreaded mixed content notification. This results in images and CSS scripts not being loaded, which means your layout will be messed up.
The most important thing to do is changing the WordPress address to the HTTPS version, as this will change most files and images to be loaded over HTTPS right away, if you use relative paths to call them.
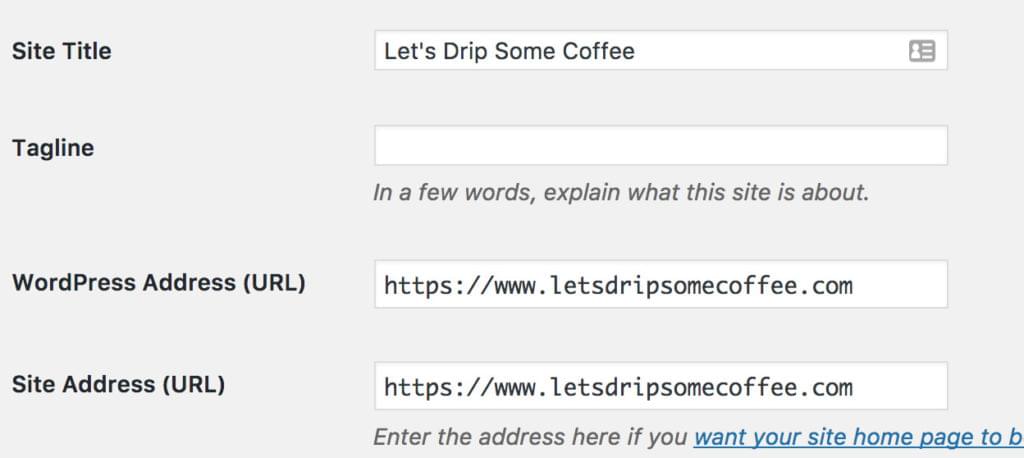
You can’t always spot straight away that you’re serving mixed content. In some cases, the padlock just won’t turn green, where in other cases it does. This has mostly to do with your browser cache. Sometimes a site may display a secure notice, but the developer console in Chrome shows otherwise. Luckily, the security tab of the console is very helpful in tracing these issues.
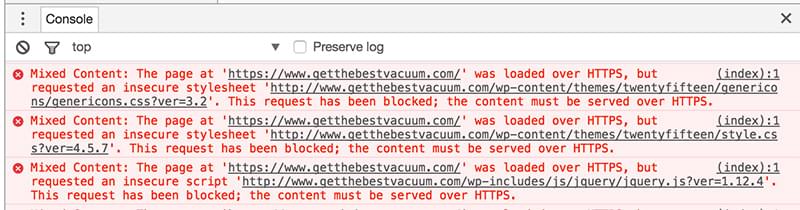
In this example, it was all a matter of changing the WordPress URL to the proper HTTPS version, after which it was all green. Another issue can be the use of absolute URLs for images, which might still be served over HTTP. There are various ways to solve this:
- Change the URLs in the database manually from HTTP to HTTPS or to relative URLs.
- Use a plugin to change the links, such as the SSL Insecure Content Fixer.
- Go through all of your images one by one, to make their paths relative.
- If you use a CDN, make sure to have that changed to SSL, or else you will still be serving insecure files.
The Ultimate Solution: Extended Validation
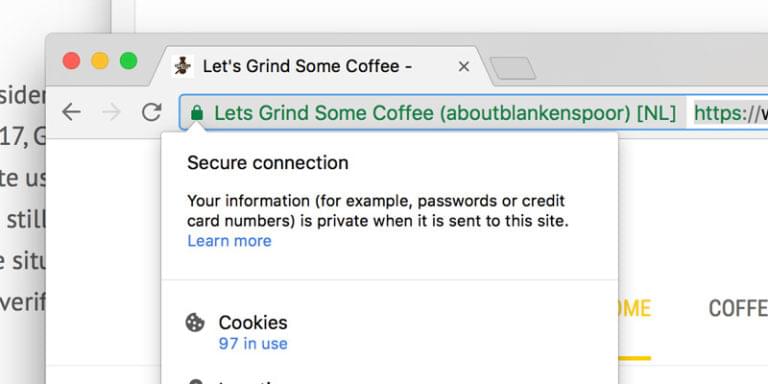
Extended Validation (EV) certificates, rather than just showing “Secure”, display your business name, indicating that you’ve gone through a process to validate that your business is, in fact, what you say it is.
An EV certificate provides the highest level of security because both the domain used and the organization behind it are vetted. It’s also backed by a warranty which compensates the end user, should the site owner (you) have obtained the certificate on fraudulent pretenses, and something goes wrong. While this warranty won’t benefit you directly, it helps to assure your visitor that you are trustworthy.
In addition, the added vanity effect this certificate has is great. For example, on mobile Safari:
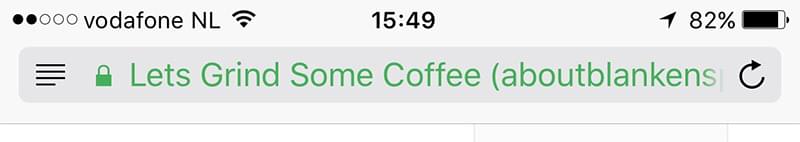
So how you get an EV SSL certificate? Well, it certainly requires more effort and paperwork than with CloudFlare and Let’s Encrypt, as it isn’t called “extended validation” for nothing!
The following steps are involved:
- Ordering the certificate
- Documents: This typically involves a signed agreement to request the certificate, identify the requester, and for the legal warranties.
- Verification of business documents: The paperwork about the business.
- Verification behind the scenes: The CA will do research to verify information about your business, and about you.
- Verification by phone: Both for the certificate requester and for the business contact.
My Experience With Extended Validation
I ordered an extended validation certificate for a website of mine, and the process went relatively smoothly. I’ve briefly documented the required steps here to give you an inside look into the process.
Step 1: Ordering the Certificate
Domain validation is part of the whole process, and NameCheap has a few steps in place to set this up, after which Comodo takes over. I ordered a Comodo EV SSL certificate, which you can get at most larger registrars, as well directly from Comodo.
Step 2: Signed Documents
I first needed to sign a certificate request by hand, which was followed up by a more extensive certificate subscriber agreement. The first form was used to identify both my company and me, as well as the domain involved. This is also where I needed to fill in my Assumed Name (Let’s Grind Some Coffee), to be used instead of my business name.
Next up was up 8-page subscriber agreement, which is used to cover the all the legal implications that come with a certificate. Both forms are used in step 4, where I had to verify myself, the application, and my business by phone.
While this document isn’t something to worry about, it is used to set the boundaries for certification fraud. All documents had to be printed, signed, scanned, and sent back.
Step 3: Verification of Business Documents
As my business was incorporated in the Netherlands, the Comodo verification team didn’t have access to the local Chamber of Commerce register. I had to send in an extract of my registration, which was a digitally signed document.
Important note about Assumed Names: If you intend to use an Assumed Name, it’s important that you have this name registered as a trade name prior to your EV application. If you don’t have a trade name registered, you can’t have an Assumed Name in your certificate.
Step 4: Verification Behind the Scenes
I don’t know all the actions which were performed as a part of their verification, of course. However, investigators can check social profiles, such as LinkedIn, use tools like Google Maps to check the physical location of your company, or potentially even send someone to the listed address to check it out.
As both I and my company were easy to find on the internet, this step didn’t cause any real delay, but depending on the circumstances, it could take longer than it did in my case.
Step 5: Verification by Phone
The final step was for them to call me to verify my request, business details and domain name, and actually speak to me. The call lasted a few minutes, where I had to answer a few verification questions like “Are you Jacco Blankenspoor?“, “For which domain name are you requesting this certificate?“.
The agent confirmed everything was correct, and that I would receive my certificate within a day. A few hours later, I received the mail containing both my certificate, as well as a Comodo Trust logo to display on my site.
The whole process requires quite a bit of paperwork. If you’re just interested in getting a regular SSL certificate, with just the green padlock and not your business name, any regular domain validated SSL certificate will do. In either case, once you have it, all you have to do then is get it uploaded to your hosting environment, which you can check your host’s support are for instructions on doing.
Conclusion
Whether you get a basic Domain Validation certification or go full-on with an Extended Validation certification to have your business name displayed, it’s now easier than it ever was before to build a secure WordPress site, and make your users feel safe.
In the end, it comes down to this:
- A CloudFlare certificate is the most convenient process of all. It will do, but given all of its downsides, this wouldn’t be my preferred choice.
- If you’re looking for basic security, a free Let’s Encrypt certificate will do and shouldn’t be too much of a hassle to get up and running. Also, it will keep Google off your back about your site being insecure.
- If maximum security and maximum customer peace of mind is what you’re after, an EV certificate is what you need.
If you have any questions, please let me know in the comments, where I am happy to help.
 Jacco Blankenspoor
Jacco BlankenspoorJacco Blankenspoor is a website developer from the Netherlands, and is currently just building lots of different websites. When he is not working on HIPAAHQ.com you might catch him grinding coffee.