
Sometimes the details make all the difference.
Typing your phone number into an online form and being told “no spaces allowed” is infuriating. It’s a tiny part of the overall user experience, but it can totally change the feeling from seamless to clunky.
Password masking is another such detail. Password masking is that familiar practice of hiding the password characters – as entered by the user – behind bullets (●), asterisks (*), or similar camouflaging characters.
The idea behind masking is to prevent nearby observers reading the password “over the user’s shoulder” and thus stolen. But there are a few significant disadvantages that may outweigh this primary advantage.
Problems with password masking
Masking the password also hides it from the user
In our attempts to maximise security, too often we severely compromise usability. There’s not much point in building a secure system if that security drives people away from using it!
Password masking is one of those examples where the by-product of security is a poorer user experience. By masking the password to protect against the vanishingly small chance a criminal is not only in the room, but no more than a few metres behind you, we’re impairing every legitimate user. This means users can’t:
- see whether they’ve typed the right thing; or
- easily correct their password if they get an error.
In turn this will mean a longer and more frustrating user experience. And these difficulties may lead users to choose far less secure – but easier to type – passwords, which poses a much more significant security risk.
“Over the shoulder” attacks aren’t as common as we may think
Bruce Schneier, world renown security specialist, says it best in his post The Pros and Cons of Password Masking:
I believe that shoulder surfing isn’t nearly the problem it’s made out to be. One, lots of people use their computers in private, with no one looking over their shoulders. Two, personal handheld devices are used very close to the body, making shoulder surfing all that much harder. Three, it’s hard to quickly and accurately memorize a random non-alphanumeric string that flashes on the screen for a second or so.
This is not to say that shoulder surfing isn’t a threat. It is. And, as many readers pointed out, password masking is one of the reasons it isn’t more of a threat. And the threat is greater for those who are not fluent computer users: slow typists and people who are likely to choose bad passwords. But I believe that the risks are overstated.
The password is still vulnerable to keylogging and malware
Unfortunately, visual masking gives the sense of more security than there actually is. While it can’t be seen, it can still be easily stolen by malware installed on the user’s device, or by a criminal using keylogging technology (which doesn’t need to be installed on the device, or even in visual proximity).
The design of some mobile operating systems eliminates some benefits of masking
When entering a password on some mobiles, each character is visible in the password field for a few seconds or until the next character is entered, whichever comes first. This means the mask is only partially applied, undermining security.
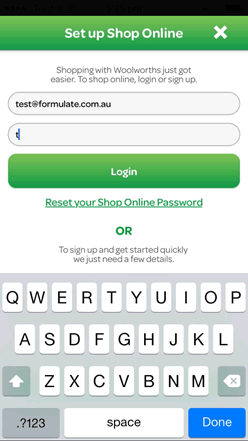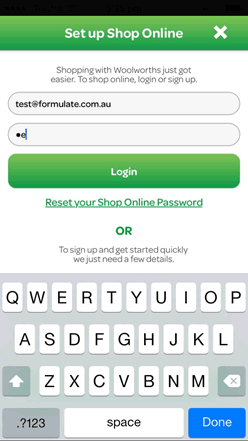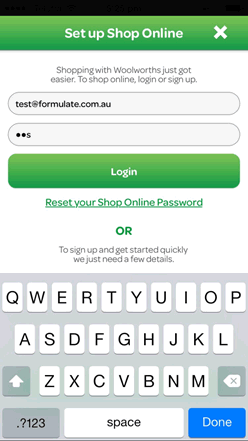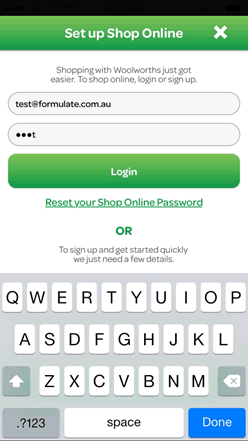
Balancing security and usability
The great news is there’s a way to maintain the security benefits of masking while improving the user experience: mask passwords by default but provide users with the ability to turn the masking off.
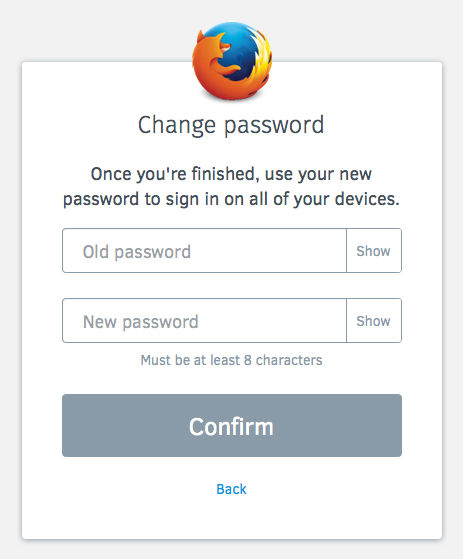
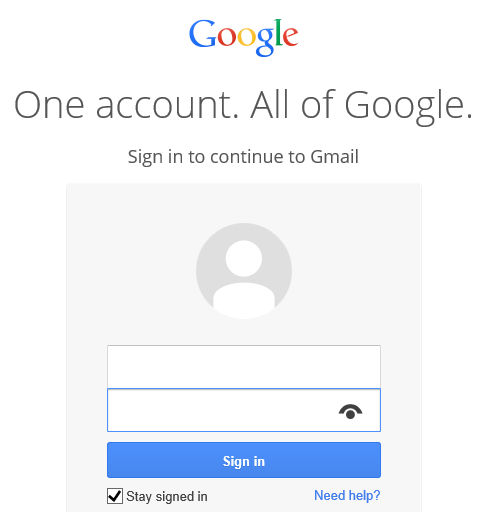

This approach:
- provides the most security by default, including against “over the shoulder” attacks;
- gives users the control over their own interaction (control being an important cornerstone in usability);
- means the interface is initially familiar to users, rather than the potential shock of presenting the password in the open (a study by Jack Holmes found 60% of users became suspicious of the site if password was unmasked by default);
- allows the user to see the password while typing or afterwards; and
- can work with any device or operating system.
The best implementation will use the words “show” and “hide”, rather than iconography that may not be intuitive. Because the user is initiating an action, ideally the “show” and “hide” will be buttons (rather than a checkbox whose label changes).

“Show password” toggle: proven results
The aforementioned study by Jack Holmes, and others, demonstrate the “show password” approach works with users. User quotes from Jack’s study include:
The fact that it is there gives me the chance to check what I have typed. It is helping me in my inability to do something simple.
and
It is protecting me against somebody looking over my shoulder. It gives me a feeling that there is some form of protection in place.
Unpublished research conducted by the Victorian Department of Justice and Regulation – with whom I have worked – also validates the “show password” approach.
So I think the time is right to start adopting this as a matter of convention. What do you think?
Frequently Asked Questions (FAQs) about Password Masking
What is the primary purpose of password masking?
The primary purpose of password masking is to protect sensitive data, such as passwords, from being seen by others. When you type your password into a form on a website, the characters are replaced with asterisks or dots. This prevents anyone looking over your shoulder, known as “shoulder surfing”, from seeing your actual password. It’s a security measure that has been in place since the early days of computing and is still widely used today.
Is password masking a hindrance to users?
While password masking is primarily a security measure, it can sometimes be a hindrance to users. The main issue is that it prevents users from seeing what they’re typing. This can lead to errors when entering the password, especially if it’s complex and includes a mix of characters, numbers, and symbols. Some users may find it frustrating if they make a mistake and have to start over because they can’t see what they’ve typed.
Are there any alternatives to password masking?
Yes, there are alternatives to password masking. One common alternative is to include a “show password” option, which allows users to toggle between hiding and showing their password. This gives users the choice of whether they want their password to be masked or not. Another alternative is to use biometric authentication methods, such as fingerprint or facial recognition, which don’t require typing a password at all.
How does password masking affect user experience?
Password masking can have both positive and negative effects on user experience. On the positive side, it can provide a sense of security, as users know that their password is being protected from prying eyes. On the negative side, it can lead to frustration if users make mistakes when entering their password and have to start over. The impact on user experience can vary depending on the individual user and the specific context.
Is password masking necessary for all types of forms?
Password masking is most commonly used for login forms, where users are required to enter their password to access an account. However, it’s not necessarily required for all types of forms. For example, in a registration form where users are creating a new password, some websites choose to show the password by default to help users ensure they’re typing it correctly. The decision to use password masking can depend on various factors, including the level of security required and the potential impact on user experience.
What are the security implications of not using password masking?
Not using password masking can potentially expose sensitive data to others. If someone is able to see your screen while you’re typing your password, they could potentially gain access to your account. However, the risk of this happening can depend on the specific context. For example, if you’re using a public computer in a busy location, the risk could be higher than if you’re using a private computer at home.
How does password masking work in mobile devices?
On mobile devices, password masking typically works in a similar way to desktop computers. When you type your password into a form, the characters are replaced with dots or asterisks. However, some mobile devices also briefly show each character as you type it before masking it, which can help you see if you’ve made a mistake.
Can password masking be disabled?
Whether or not password masking can be disabled can depend on the specific website or application. Some websites and applications include a “show password” option, which allows you to toggle between hiding and showing your password. However, not all websites and applications offer this option.
What is the future of password masking?
The future of password masking is uncertain. While it’s still widely used today, there are ongoing debates about its effectiveness and impact on user experience. Some experts argue that other security measures, such as two-factor authentication and biometric authentication, are more effective and user-friendly. However, it’s likely that password masking will continue to be used in some form for the foreseeable future.
How does password masking contribute to overall online security?
Password masking is just one of many measures that can contribute to overall online security. By preventing others from seeing your password, it can help protect your account from unauthorized access. However, it’s important to remember that password masking is not a foolproof solution and should be used in conjunction with other security measures, such as using strong, unique passwords and enabling two-factor authentication.
Jessica Enders has suffered from a life long condition known as a love of designing forms and other transactional interfaces. She is attempting to minimise the adverse symptoms by running her own form design business, Formulate Information Design.


