 Wireshark is a network protocol analyzer for Unix and Windows. I have only brushed the surface with this tool so far but it comes in handy when performing analysis on http requests between your machine and others on the network.
http://www.wireshark.org/
Wireshark is a network protocol analyzer for Unix and Windows. I have only brushed the surface with this tool so far but it comes in handy when performing analysis on http requests between your machine and others on the network.
http://www.wireshark.org/
Before you start
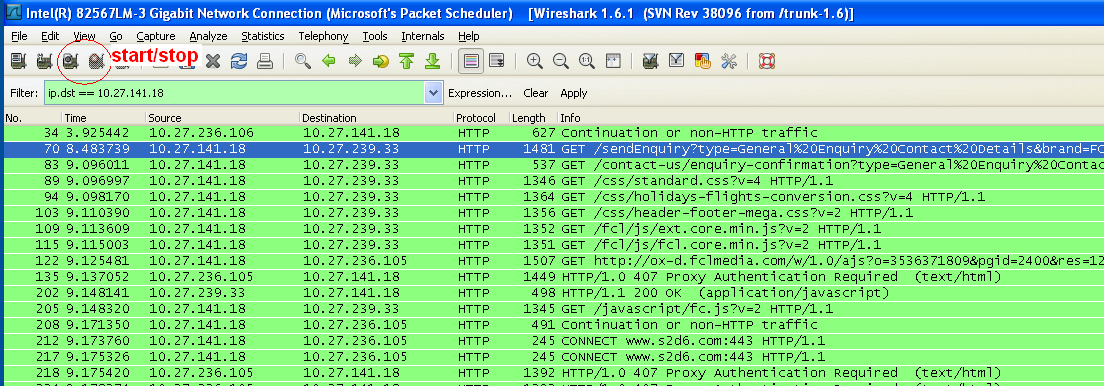
- Wireshark captures every request so only click start when you are ready to capture and click stop when your finished
- You’ll need your IP address
Basic Instructions
- Download, install, run
- Click start to capture requests
- Use the expression filter to find your requests, here are some common filters:
- ip.addr == 10.27.999.99 (for example)
- ip.dst == 10.27.999.99 (for example)
- Find the request you want to analyse and Right click > Follow TCP Stream
- This should bring up the request in full
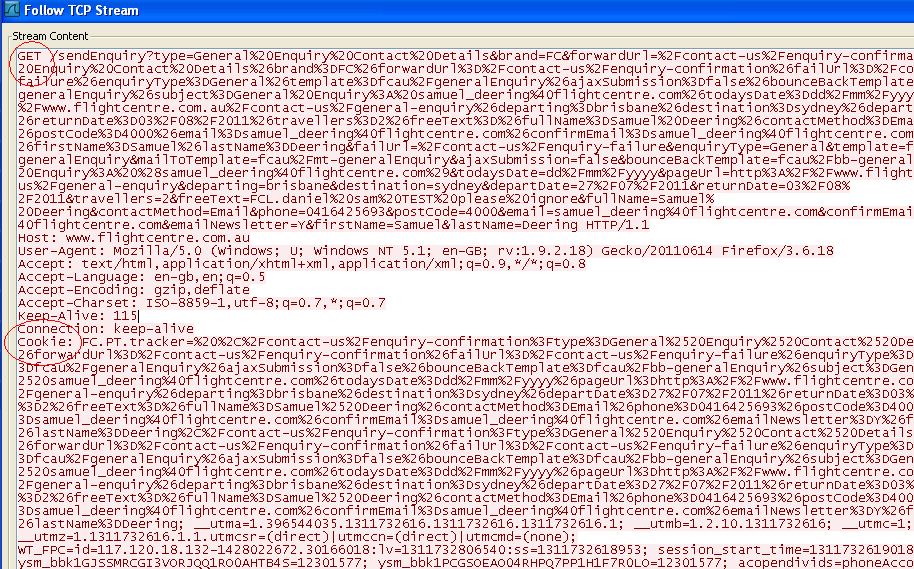
Frequently Asked Questions (FAQs) about Wireshark Deep HTTP Request Analysis
What is Wireshark and why is it important for HTTP request analysis?
Wireshark is a widely used network protocol analyzer that allows users to see what’s happening on their network at a microscopic level. It is essential for HTTP request analysis because it provides detailed insights into the data being transmitted over a network. This includes the ability to view the source and destination of packets, the protocols being used, and the data contained within these packets. This information can be invaluable for troubleshooting network issues, identifying security threats, and optimizing network performance.
How can I use Wireshark to analyze HTTP requests?
To analyze HTTP requests with Wireshark, you first need to start a new capture session. Once the session is running, you can filter the captured data to only show HTTP requests. This can be done by typing “http” into the filter bar and pressing enter. You can then click on any of the displayed packets to view detailed information about the HTTP request, including the request method, URL, and headers.
What information can I get from an HTTP request analysis in Wireshark?
An HTTP request analysis in Wireshark can provide a wealth of information. This includes the request method (GET, POST, etc.), the requested URL, the HTTP version, and any headers included in the request. Additionally, if the request includes a message body (such as a POST request), you can view this data as well.
How can I filter HTTP requests in Wireshark?
Wireshark provides a powerful filtering system that allows you to narrow down the displayed packets to only those that are relevant to your analysis. To filter HTTP requests, simply type “http” into the filter bar and press enter. You can also use more advanced filters to display only requests to a specific URL, requests using a specific method, or requests that include a specific header.
Can Wireshark analyze encrypted HTTP requests?
Yes, Wireshark can analyze encrypted HTTP requests, but it requires some additional setup. You need to configure Wireshark with the necessary encryption keys and ensure that it is set up to decrypt the specific type of encryption being used. Once this is done, Wireshark can decrypt the encrypted packets and display the HTTP request data.
How can I save my HTTP request analysis in Wireshark?
Wireshark allows you to save your analysis for later review. To do this, simply go to the “File” menu and select “Save”. You can choose to save the entire capture, or only the displayed packets (if you have applied a filter). The saved file can then be opened later for further analysis.
Can Wireshark help me identify network security threats?
Yes, Wireshark can be a valuable tool for identifying network security threats. By analyzing the data being transmitted over your network, you can identify suspicious activity, such as unusual traffic patterns, attempts to access sensitive resources, or the transmission of malicious data.
How can I view the response to an HTTP request in Wireshark?
To view the response to an HTTP request in Wireshark, you need to locate the corresponding HTTP response packet. This can usually be found immediately after the request packet in the packet list. Clicking on the response packet will display detailed information about the response, including the status code, headers, and any response data.
Can I use Wireshark to analyze other protocols besides HTTP?
Yes, Wireshark supports analysis of a wide range of network protocols, not just HTTP. This includes protocols such as TCP, UDP, ICMP, and many others. You can select the protocol you want to analyze using the filter bar.
How can I learn more about using Wireshark for HTTP request analysis?
There are many resources available for learning more about using Wireshark for HTTP request analysis. This includes the official Wireshark documentation, online tutorials, and community forums. Additionally, many books and training courses are available that cover this topic in depth.
 Sam Deering
Sam DeeringSam Deering has 15+ years of programming and website development experience. He was a website consultant at Console, ABC News, Flight Centre, Sapient Nitro, and the QLD Government and runs a tech blog with over 1 million views per month. Currently, Sam is the Founder of Crypto News, Australia.



