The Android Operating System is an open platform based on Linux, integrated into mobile devices, smart watches, tablets and even televisions and cars. The opportunity to create applications across a myriad of devices raises the problem of security, which I believe to be Android’s biggest challenge.
Android maintains application level security by using a full permissions based security mechanism that lets users restrict access to application components. Permissions can prevent malicious applications from corrupting data, gaining access to sensitive information, or making excessive or unauthorized use of hardware resources or external communication channels.
By default no Android application has permissions to perform any operation that would impact the operating system, the users private data or other applications. But without permission to use anything, an Android Application is not a useful application.
The Security issue
Android uses permissions to filter the capabilities of an application and it’s up to the user whether to accept the permissions of an application upon installation. The problem is that users tend to not read permissions and accept them thoughtlessly. This can lead to a range of security issues from private information flowing to the Android operating system and worse, kernel alterations.
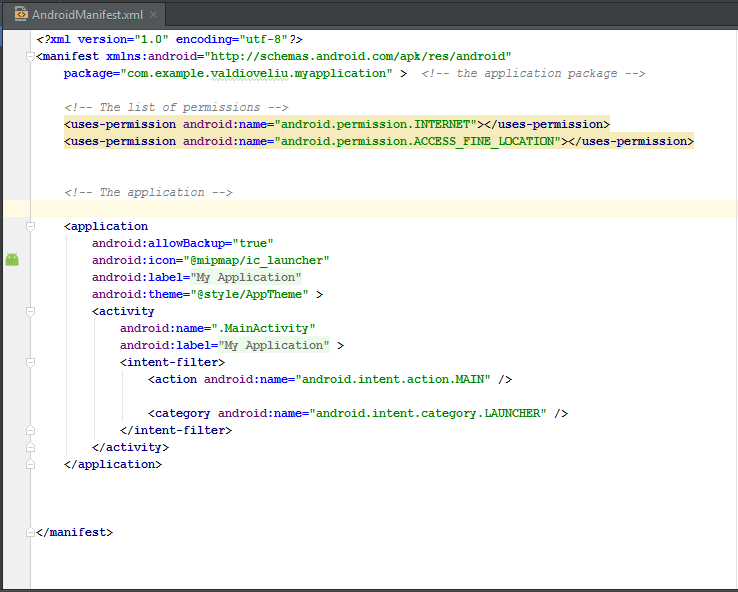
In this article I will discuss the Android manifest and permissions. The manifest file contains information on the app package, including permissions, content providers, services, activities and broadcast receivers.
Here is a general structure of the manifest file to show where permissions go in the manifest.
The most dangerous application permissions
To judge what permissions to accept, every user must keep the function of installed applications in mind. For example “Why does a Game need permission for my contacts or asks for permission to send SMSs?”. You don’t need to send SMSs in a Game. Such permissions tend to be dangerous and leak private user information.
Permissions you might want to reconsider
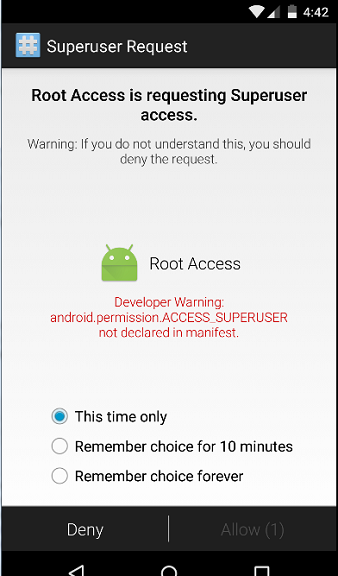
1. Root Permission
The root user is the system administrator and has control throughout the system, without limits. By default the android user does not have access to the root properties because inexperienced users can do serious damage to their operating system. Root privileges are gained by a process called “Rooting the Android device”. There are no limitations in what a malicious application can do when they get this permission from the root user.
Here is a small example of an application running a shell script with superuser permissions for rebooting the android device.
try {
String[] reboot = new String[] { "su", "-c", "reboot" };
//-c will cause the next argument to be treated as a command
Process process = Runtime.getRuntime().exec(reboot);
process.waitFor(); //wait for the native process to finish executing.
} catch (Exception e) {
Toast.makeText(getApplicationContext()," Device not rooted.\n Could not reboot...",Toast.LENGTH_SHORT).show();
}By using the “su” command the application will run with the privileges of the SUPER USER and if the device is rooted it will reboot.

When the code is run on a non-rooted device, a toast message will appear.
If you do want to add this permission to an application then add the following line to your manifest file.
<uses-permission android:name="android.permission.ACCESS_SUPERUSER"></permission>2. Read/Write personal data permissions
There are some permissions that allow an application to use personal data of the user. If you want information to be private try to avoid these permissions in the Android Manifest file.
<uses-permission android:name="android.permission.READ_CALENDAR"></uses-permission>
<uses-permission android:name="android.permission.WRITE_CALENDAR"></uses-permission>
<uses-permission android:name="android.permission.READ_CALL_LOG"></uses-permission>
<uses-permission android:name="android.permission.WRITE_CALL_LOG"></uses-permission>
<uses-permission android:name="android.permission.READ_CONTACTS"></uses-permission>
<uses-permission android:name="android.permission.WRITE_CONTACTS"></uses-permission>3. Financial permissions
Some permissions can cost users money if they are unwittingly granted. Those most relevant to mobile phone apps are SMS/MMS permissions and call permissions. These can send SMSs in the background and call phone numbers, even without going through the Dialler application. These permissions can allow an application to read SMSs and MMSs in the background unseen by the user.
The permissions needed for SMS, MMS and Call operations are:
<uses-permission android:name="android.permission.SEND_SMS"></uses-permission>The permission used to send SMS and MMS messages.
<uses-permission android:name="android.permission.CALL_PHONE"></uses-permission>The permission used to initiate a phone call.
Here is a simple example of how to send a SMS to a specified number.
String message = "Hello Android fans! ";
String number = "xxxxxxxxxxxx";
//it is preferable to use a complete international number
SmsManager.getDefault().sendTextMessage(number, null, message, null, null);Remember this code will only work if this permission is included in the manifest file.
<uses-permission android:name="android.permission.SEND_SMS"></uses-permission>4. Location permission
Location permissions allow an application to access a user’s location at any time: – Access coarse location: Applications can access approximate location derived from cell towers and Wi-Fi. – Access fine location: Applications can access a precise location from location sources such as GPS, cell towers, and Wi-Fi.
The permissions needed to work with location are:
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION"></uses-permission>To access approximate location.
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"></uses-permission>To access precise location.
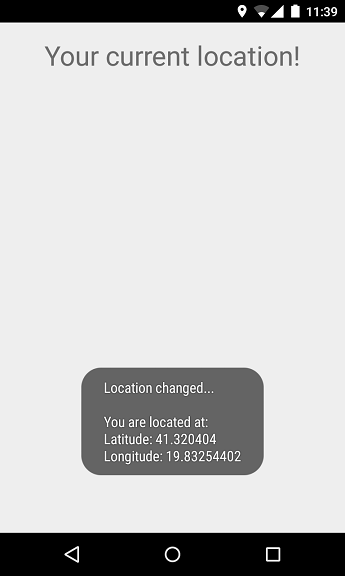
Here is how to get the precise location of an Android device:
public class MainActivity extends Activity implements LocationListener {
private LocationManager locationManager;
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
locationManager = (LocationManager) getSystemService(Context.LOCATION_SERVICE);
locationManager.requestLocationUpdates(LocationManager.GPS_PROVIDER,
3000, 10, this);
}
@Override
public void onLocationChanged(Location location) {
String myLocation ="Location changed...\n\nYou are located at: " + "\nLatitude: " + location.getLatitude()
+ "\nLongitude: " + location.getLongitude();
Toast.makeText(getApplicationContext(), myLocation, Toast.LENGTH_LONG).show();
}
@Override
public void onProviderDisabled(String provider) {
Intent intent = new Intent(Settings.ACTION_LOCATION_SOURCE_SETTINGS);
startActivity(intent);
Toast.makeText(getApplicationContext(), "Gps is turned off... ",
Toast.LENGTH_SHORT).show();
}
@Override
public void onProviderEnabled(String provider) {
Toast.makeText(getApplicationContext(), "Gps is turned on... ",
Toast.LENGTH_SHORT).show();
}
@Override
public void onStatusChanged(String provider, int status, Bundle extras) {
}
}To run this code you have to include this permission to access the precise location:
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"></uses-permission>The java MainActivity class implements LocationListener to obtain location information from the device.
In the onCreate() method requestLocationUpdates() is called to get the current location of the device and every time it changes, onLocationChanged() is called and the new location is displayed.
The onProviderDisabled() method is called if the device GPS is disabled, redirecting the application to the location settings of the device.
5. Audio and video permissions
These mean that someone can listen to a conversation or use a phone camera to surveil the user. Examples are:
The permissions required in a manifest file are:
<uses-permission android:name="android.permission.CAMERA"></uses-permission>
<uses-permission android:name="android.permission.CAPTURE_VIDEO_OUTPUT"></uses-permission>
<uses-permission android:name="android.permission.CAPTURE_AUDIO_OUTPUT"></uses-permission>
<uses-permission android:name="android.permission.RECORD_AUDIO"></uses-permission>6. Package Installation
These can install additional packages onto a phone without the user knowing. The user doesn’t need to accept them because the application has the permission to do so.
<permission android:name="android.permission.INSTALL_PACKAGES"></permission>7. Kill background processes
These allow an application to call killBackgroundProcesses(String), which gives an application the power to kill others running in the background.
<uses-permission android:name="android.permission.KILL_BACKGROUND_PROCESSES"></uses-permission>What is Google up to next?
Last month Google announced Android M during Google I/O 2015. Android M has many innovations including a new Application Permissions mechanism. Permissions will be requested the first time a user tries to use a feature, not at the point of installation. Making developer and user experience much better.
Frequently Asked Questions (FAQs) about Android App Permissions
What are the most risky Android app permissions to grant?
The most risky Android app permissions to grant are those that can access your personal data and sensitive information. These include permissions to access your contacts, messages, location, camera, microphone, and storage. Granting these permissions can potentially expose your personal data to third-party apps, which can misuse it for malicious purposes. Therefore, it’s crucial to only grant these permissions to trusted apps.
How can I manage app permissions on my Android device?
You can manage app permissions on your Android device by going to the settings menu, then selecting ‘Apps & notifications’. From there, you can select the app whose permissions you want to manage. You can then see all the permissions the app has and toggle them on or off as needed.
What does the ‘android.permission.ACCESS_SUPERUSER’ permission mean?
The ‘android.permission.ACCESS_SUPERUSER’ permission is a special permission that grants an app root access to your device. This means the app can perform actions and access data that are normally restricted. This permission is typically used by system-level apps and should be granted with caution, as it can potentially harm your device if misused.
How can I grant an app root access without GUI interaction?
Granting an app root access without GUI interaction can be done using ADB (Android Debug Bridge) commands. However, this process is complex and should only be performed by advanced users, as it can potentially harm your device if done incorrectly.
What is the ‘AndroidManifest.xml’ file and what does it do?
The ‘AndroidManifest.xml’ file is a crucial file in an Android app that contains information about the app’s components, permissions, and other essential details. This file is read by the Android system during the installation of the app to understand how to integrate the app into the system.
How can I get root access on my Android device?
Getting root access on your Android device can be done using a process called ‘rooting’. This process involves unlocking the device’s bootloader, installing a custom recovery, and then flashing a root access granting app like SuperSU. However, this process is complex and risky, and can potentially brick your device if done incorrectly.
What are the potential risks of granting an app root access?
Granting an app root access can potentially expose your device to various risks. These include the risk of bricking your device, voiding your warranty, exposing your personal data to third-party apps, and making your device more vulnerable to malware and other security threats.
How can I protect my device from risky app permissions?
You can protect your device from risky app permissions by only downloading apps from trusted sources, carefully reading the permissions an app requests before installing it, and regularly reviewing and managing the permissions of the apps installed on your device.
What is the difference between normal and dangerous permissions in Android?
In Android, permissions are categorized into two types: normal and dangerous. Normal permissions are those that pose minimal risk to the user’s privacy and are granted automatically by the system. On the other hand, dangerous permissions are those that can access sensitive data and are only granted upon the user’s explicit approval.
Can I revoke an app’s permissions after granting them?
Yes, you can revoke an app’s permissions after granting them. You can do this by going to the settings menu, then selecting ‘Apps & notifications’. From there, you can select the app whose permissions you want to revoke and toggle them off.
 Valdio Veliu
Valdio VeliuValdio recently graduated in Computer Engineering. He is a mobile developer, who is passionate about mobile technologies and learning new things. He has worked with languages such as C, Java, php and is currently focused on Java, mobile and web development