“Web attacks are the greatest threat facing an on-line business today.” This statement may seem overwhelming and yet, over the last few years, we have witnessed many high-profile web attacks that have actually brought down businesses of all sizes – massive-scale data breaches that caused almost irreparable damage to company image, brand value and user trust. For another take on the scope of this problem, one can refer to a recent estimate made by Keith Alexander, Director of the US National Security Agency, who put an incredible annual price tag on total value of time wasted and opportunities lost in the US alone due to cyber-crime – a whopping $388 billion. Perhaps one of the most alarming and new aspects of cyber-crime today is that the attackers are changing their focus, targeting not only big and prominent websites, but also small and medium businesses. These sites, who until recently were mostly unconcerned with cyber-security, present an easy target for any would-be attacker. As such, several recent security studies show that the number of cyber-attacks on SMB websites in 2012 has doubled, and the numbers continue to grow. Luckily, SMB website owners and operators are becoming aware of the numerous security threats and are proactively seeking affordable yet still effective means for online protection. When choosing an online security solution, SMBs should take a multi-layered security approach – starting from simple Bad bot & Automation Protection and moving forward to encompass WAF and DDoS Solutions.
Incapsula: Automation & Bad bot Protection
Bots are non-human entities that operate with various, often malicious, purposes. Recent research by Incapsula showed that on average 51% of web site traffic comes from these non-humans – with 31% of potentially damaging automated traffic from various hackers, scrapers, spammers and vulnerability scanners often used as a vanguard force for a more devastating attack.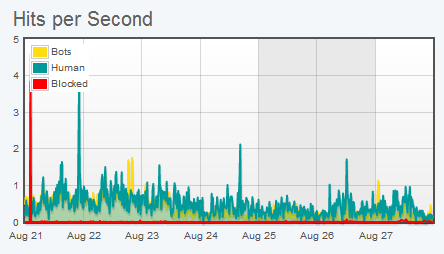
Incapsula Dashboard: Traffic report
Incapsula’s first layer of protection identifies and filters out malicious bots. Since many such bots will try to disguise themselves with fake user-agents and spoofed IPs, the system uses numerous identification techniques, looking for clues in the HTTP Headers and in bot behavior patterns. If needed, the system will also apply a set of challenges: starting with a cookie support challenge, moving on to a JS support challenge and in certain cases even using CAPTCHAs for definitive human identification. All the collected data is gathered and preserved as a “bot signature,” making subsequent bot identification faster and more reliable. Over the years, Incapsula has gathered a large pool of bot data, which was recently consolidated in Botopedia.org – a community-based directory that shares bot information freely, with all who require it. Users can customize Bot Protection, with an option for white-listing or blacklisting based on user-agent, IP of origin, type of application used (e.g. white-listing of all CURL access) and more. Incapsula Settings: IP and Country blocking rules
Incapsula Settings: IP and Country blocking rules
Incapsula Settings: Bot Blacklisting/Whitelisting rules
The rules management GUI is built to be quick and intuitive, using check-boxes and auto-completion features to keep things simple. The system also offers a detailed event log to help keep track of recent bot related activity.Web Application Firewall (WAF)
Incapsula’s PCI DDS compliant WAF serves as second line of defense and protects the website and its database from advanced web threats. To deal with these threats, Incapsula’s WAF monitors user input and application behavior, employing a wide set of security rules to identify and mitigate different attack vectors, and using cross-referencing to prevent false-positives. The WAF rules are regularly updated. As a result, this firewall can deal with a large number of existing threats and expand its reach to handle new threats as they arise. Here is how Incapsula’s WAF protects from the most common OWASP Top 10 Threats:|
Threat |
Incapsula’s Solution |
| A1: Injections – Injection flaws, particularly SQL injection, are common in web applications. Injection occurs when user-supplied data is sent to an interpreter as part of a command or query. The attacker’s hostile data tricks the interpreter into executing unintended commands or changing data. | Incapsula can detect and block injection attacks through validation of user input using either negative or positive security policies. |
| A2: Cross-Site Scripting (XSS) – XSS flaws occur whenever an application takes user supplied data and sends it to a web browser without first validating or encoding that content. XSS allows attackers to execute script in the victim’s browser which can hijack user sessions, deface web sites, introduce worms, etc. | Incapsula detects and blocks Cross Site Scripting (XSS) attacks through validation of user input using either negative or positive security policies. |
| A3: Broken Authentication & Session Management Account credentials and session tokens are often not properly protected. Attackers compromise passwords, keys, or authentication tokens to assume other users’ identities. | Incapsula detects and blocks Insecure Direct Object Reference attacks through validation of user input against known attack vectors, behaviors, and deviations. Incapsula also analyzes the desired application behavior and access rules, applying specific policies per customer application. |
| A5: Cross-Site Request Forgery (CSRF) – A CSRF attack creates forged HTTP requests and tricks a victim into submitting them via image tags, XSS, or other techniques. If the user is authenticated, the attacker succeeds. CSRF takes advantage of Web applications that allow attackers to predict all the details of the transaction. Since browsers send credentials like session cookies automatically, attackers can create malicious web pages which generate forged requests that are indistinguishable from legitimate ones. | Incapsula constantly monitors referral usage patterns and in conjunctions with its other external feeds, uses a blacklisting security model to detect potential malicious behavioral patterns and offending sites. |
| A6: Security Misconfiguration – Security misconfiguration can happen at any level of an application attack, including the platform, web server, application server, framework, and custom code. Such flaws can give attackers access to default accounts, unused pages, unpatched flaws, unprotected files, and directories to gain unauthorized access to system data. | Incapsula applies both generic and application specific security measures to accommodate for security misconfiguration. This mitigates administrative and other access vulnerabilities and also includes application specific “virtual patching”. |
| A7: Insecure Cryptographic Storage – Many web applications do not properly protect sensitive data such as credit cards, Social Security Numbers (SSNs), and authentication credentials with appropriate encryption or hashing. Attackers may use this weakly protected data to conduct identity theft, credit card fraud, or other crimes. | Incapsula does not directly store confidential data. |
| A8: Failure to Restrict URL Access – Frequently, an application only protects sensitive functionality by preventing the display of links or URLs to unauthorized users. Attackers can use this weakness to access and perform unauthorized operations by accessing those URLs directly. | Incapsula applies application specific, as well as signature and client based illegal resource access policies. |
| A9: Insufficient Transport Layer Protection – Applications frequently fail to encrypt network traffic when it is necessary to protect sensitive communications. | Incapsula fully support HTTPS Traffic. Incapsula is able to terminate HTTPS traffic, inspect it and re-encrypt the traffic, prior to transmitting it to the protected host. Incapsula also ensures the level of encryption of the SSL protocol (such as encryption strength). |
| A10: Invalidated Redirects and Forwards – Applications frequently fail to encrypt network traffic when it is necessary to protect sensitive communications. | Incapsula analyzes the application behavior, mitigating known security vulnerabilities, such as unauthenticated redirects and forwards. |
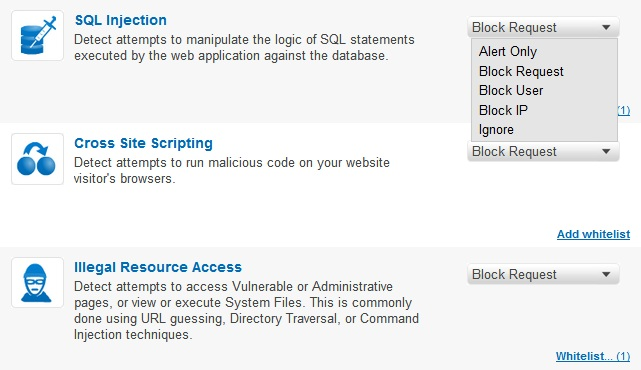
Incapsula Settings: WAF custom Rules Screen
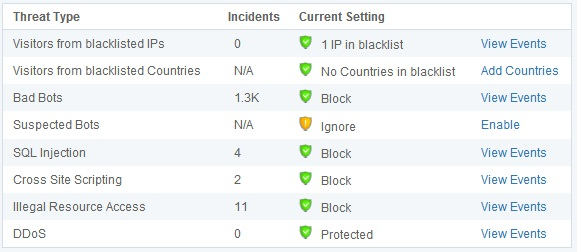 Incapsula Dashboard: Security Threat Monitoring
Incapsula Dashboard: Security Threat Monitoring
DDoS Mitigation Services
Incapsula’s Enterprise plan offers full protection against all types of DDoS threats, including network-based (Layer 3 – 4) attacks, like SYN or UDP floods, and application (Layer 7) attacks that attempt to overwhelm server resources. The service can also block advanced attacks that exploit application and web server vulnerabilities, such as Slowloris DDoS, HTTP Flood, Apache Killer and etc. Incapsula’s global network of scrubbing centers is able to scale on demand to counter multi-gigabyte DDoS attacks. As this is cloud service, the mitigation is applied outside of the client’s network, allowing only filtered traffic to reach the hosts. Incapsula’s bot identification capabilities help mitigate application (Layer 7) DDoS attacks, where the DDoS requests look like legitimate visitor sessions. While most DDoS protection services are based on easy-to-evade and false positive-prone techniques, like rate limiting or showing an annoying delay screen to every visitor, Incapsula can actually differentiate between humans and bots, thus ensuring that legitimate visitors can continue to access the site unimpeded.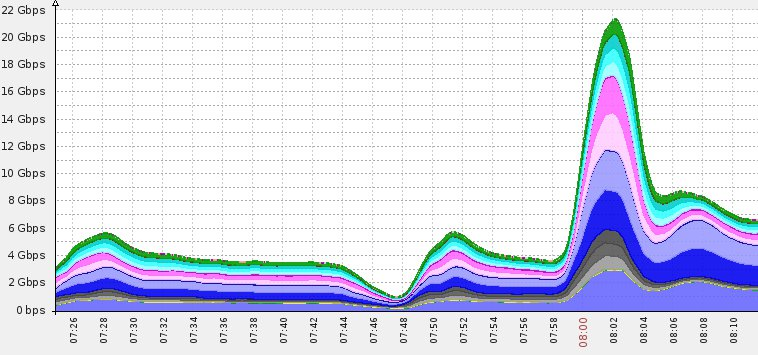
22Gbps DDoS attack mitigated across scrubbing centers.
In Conclusion:
Incapsula’s message is that of “affordable high-end security” and it delivers on its promise. While implementing its “economy of scale” principles, Incapsula protects websites by leveraging a collective knowledge base of known threats, including new and emerging attack methods. Working behind the scenes, the Incapsula security team makes sure that all new information is aggregated across the entire service network, for the benefit of all service users.Frequently Asked Questions (FAQs) about Incapsula
What is Incapsula and how does it work?
Incapsula is a cloud-based application delivery platform that provides multiple security layers for websites. It works by routing a website’s traffic through its global network of high-powered servers. This process enables Incapsula to identify and block potential threats before they reach the website. It also optimizes the website’s performance by caching its content and delivering it directly from the nearest server to the site visitor.
How does Incapsula differ from other website security solutions?
Unlike traditional website security solutions, Incapsula offers a multi-layered security approach. This includes a web application firewall to block hacking attempts, DDoS protection to ensure your website remains accessible during an attack, content delivery network to speed up website load times, and a load balancer to distribute traffic evenly across your servers.
Is Incapsula easy to set up?
Yes, setting up Incapsula is straightforward. It doesn’t require any hardware, software, or changes to your website’s code. All you need to do is change your website’s DNS settings to route your traffic through Incapsula’s network.
How does Incapsula’s Content Delivery Network (CDN) improve website performance?
Incapsula’s CDN improves website performance by caching its content and serving it to visitors from the nearest server. This reduces the distance that data has to travel, resulting in faster load times. The CDN also compresses website data, further improving speed and performance.
What types of threats can Incapsula protect against?
Incapsula can protect against a wide range of threats, including Distributed Denial of Service (DDoS) attacks, SQL injection, cross-site scripting (XSS), illegal resource access, and other OWASP top 10 threats.
Can Incapsula handle high traffic websites?
Yes, Incapsula is designed to handle high traffic websites. Its load balancing feature ensures that traffic is evenly distributed across your servers, preventing any one server from becoming overloaded.
Does Incapsula offer any reporting or analytics?
Yes, Incapsula provides detailed analytics about your website’s traffic and security. This includes information about threats that have been blocked, traffic volumes, visitor locations, and more.
Is Incapsula suitable for e-commerce websites?
Absolutely. Incapsula’s security features are particularly beneficial for e-commerce websites, which often handle sensitive customer data. Its PCI-certified web application firewall helps to protect this data from security threats.
How does Incapsula’s DDoS protection work?
Incapsula’s DDoS protection works by identifying and blocking malicious traffic. It uses a combination of rate-based heuristics, reputation-based security rules, and progressive challenges to distinguish between legitimate and malicious traffic.
Can I use Incapsula with my existing hosting provider?
Yes, Incapsula is compatible with all hosting providers. It operates independently of your hosting service, providing an additional layer of security and performance optimization.
Product Evangelist at Incapsula Inc, and an online marketing expert with over 10 years of SEO/SEM and Social Marketing experience. In his past he served as a Department Manager at a Webhosting Company, and later as a CTO of a prominent Advertising Firm. He’s also a proud father, an award winning author, an overly enthusiastic gamer and a dog person



