We all heard the rumors regarding NSA mass espionage over the internet using the MITM (man in the middle) technique, or if anyone didn’t read about, in few Google searches can find the whole story.
This article is intended for people who use Mozilla, does not involve the use of VPNs and just simply reveals how to configure some settings in the Firefox browser to increase safety when traffic decryption is attempted.
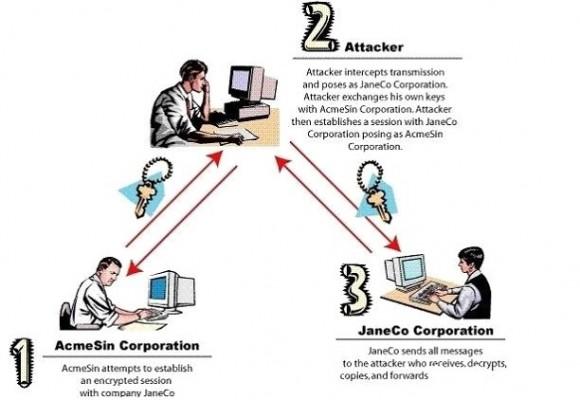
If you don’t know anything about MITM attacks, take a look over the following image that illustrates very well the concept of these kind of attacks (feel free to read more about, the subject is discussed extensively in a lot of forums, blogs, articles).
The first thing I recommend is to install this add-on for Firefox:
https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/
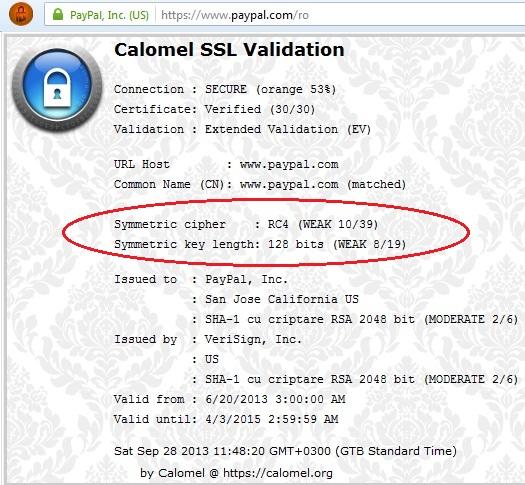
The add-on is very useful because:
- it allows you to see how strong the encryption used on sites visited is, in a very simple style
- it allows you to see in detail how the encryption was done, using “points” for the algorithms used
- it allows you to make change useful settings.
While I was researching this article, I noticed that major sites including Facebook, Google, Paypal and so on, provide by default a very weak encryption: RC4 – 128 bits!
More details about the RC4 algorithm and its problems can be found here.
Let’s take a look at SSL/TLS
I do not want this article to turn into an article about SSL / TLS, but I must say a few basic things.
- SSL / TLS are some protocols and rules that must be met in order to achieve a secure connection between your computer and the site you visit. TLS is basically an upgraded version of SSLs.
- SSL versions 1.0, 2.0 and 3.0 are old and should not be used, especially since it is known that they have security problems. TLS 1.0 is an enhanced version of SSL 3.0 and TLS 1.1 and TLS 1.2 are newer versions of TLS.
Creating a SSL connection is as follows:
- TCP connection is made
- The client (browser) sends “Client Hello” to the server. Also sends its SSL / TLS version. i.e. TLS 1.0
- The server responds with “Hello World” also specify supported encryption version, (i.e.TLS 1.0) and TLS chosen cipher suite(algorithm used for Encryption)
- The server sends the certificate (or certificates) to identify. Specifically, says: “Look, this is a proof that I am “www.sitepoint.com”. In order to be recognized by the browser as valid, the certificates must be signed by an authority in this field: VeriSign and other companies recognized as legitimate to sign certificates
- The client verifies that the received certificate is okay, and if everything is fine, client and server exchanges keys (handshake).
Using keys exchanged above data encryption is performed using symmetric encryption algorithm (AES for example) using the change in “Key Exchange”. The size depends on the cipher-suite keys. (For example, on 128-bit AES encryption, to bruteforce the data sent, it is necessary to attempt 2 ^ 128 keys; BUT If the algorithm is RC4, there are many known attacks against this algorithm, so the chances are much greater that such encryption can be broken in a shorter time.)
What can we do?
As I said, by default, browsers send the full list of cipher-suite and server usually choose a simple and fast algorithm as RC4, for page loading speed and compatibility with older browsers. We can force the browser to choose a stronger cipher simply by changing the list of cipher-suites that the browser sends to the server, eliminating “weak” cipher like RC4.
To do that, go to the configuration page in Firefox with about:config (in the url), after that, search for security.ssl.
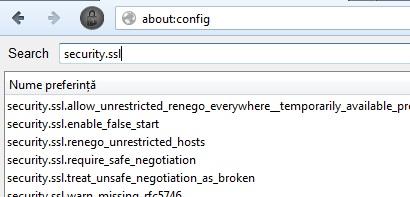
From here we can disable certain cipher suites. I cannot say with certainty which are safe and which are not, but I can recommend you to choose RSA (key exchange) and AES (256-bit). I have disabled all except RSA_AES_256_SHA.
The result
Close the browser and reopen it and:
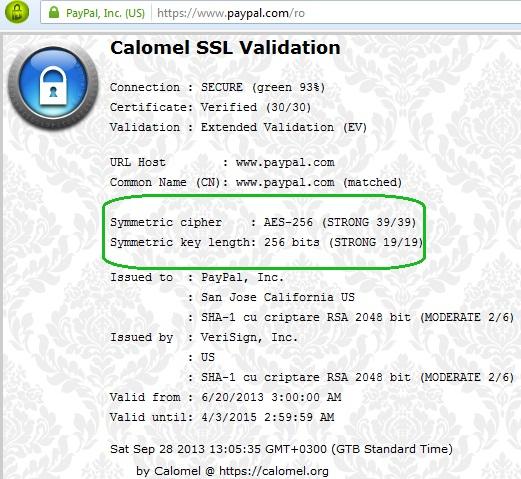
I hope this information will help you to browse over the internet in a safe way, avoiding at least MTIM attacks.
Resources
- SSL/TLS – http://en.wikipedia.org/wiki/Transport_Layer_Security
- MITM – http://en.wikipedia.org/wiki/Man-in-the-middle_attack
- Calomel – https://addons.mozilla.org/ro/firefox/addon/calomel-ssl-validation/
 Adrian Birsan
Adrian BirsanAdrian Birsan is the lead developer and founder of www.Softpill.eu. In addition he is an experienced Information Security Professional, network administrator, guitar player and all around problem solver.
